From time to time GovEvents will come across information we feel our members and audience would benefit from. Here's something we wanted to share:
Online privacy is a topic that grows in importance every single year. With more and more web services, connected apps, and even home assistant devices that are gaining in popularity, it's now more crucial than ever to understand what the dangers to your online privacy are and how to protect it consciously.
This online privacy guide is all about that.
Here are 19 actionable steps to help you remain anonymous on the web and protect your online privacy. No sophisticated computer knowledge required.
5. Get a VPN
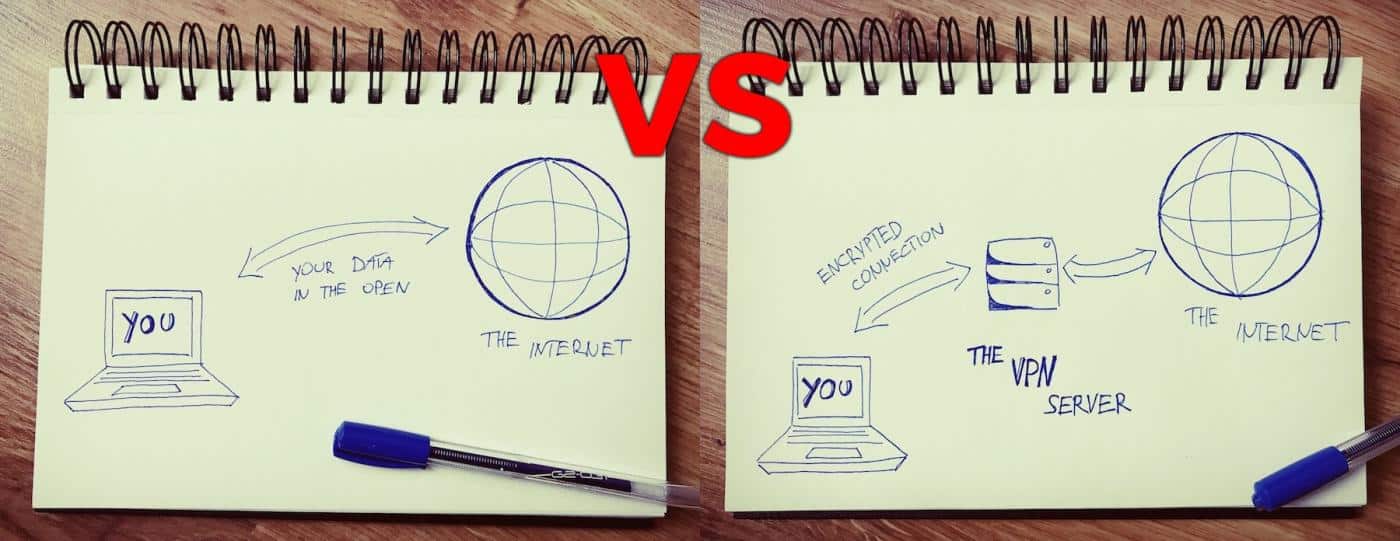
Normally, your connection to the web is unprotected by anything. It's just your computer requesting a website (or a service, or a tweet, etc.) and then the server providing that website to you.
What's problematic from an online privacy point of view here is that such a connection is public, can be intercepted, and every server helping on with the connection along the way can take a peek into what's being transmitted. If it's a sensitive email (or anything to that nature) then you really don't want that.
This is where a VPN comes into play. VPN (or Virtual Private Network) is a service that allows you to connect to the web safely by routing your connection through a VPN server before it gets to its destination.
Here's a quick visualization of what your connection looks like without and then with a VPN enabled:
What a VPN actually does is encrypting the connection so that even if someone intercepts it, the information within will be scrambled and unreadable. In fact, no intercepting party will be able to determine where the connection is coming from or what it is about, thus giving you improved online privacy.
Even though the concept might seem complicated and intimidating at first, modern VPNs are actually very easy to use and don't require any technical skills like server configuration or routing. All you need to do is literally install your VPN of choice and enable it with a single click.
We have a comparison of the best VPNs on the market right here. Many of the top VPN solutions also offer versions for mobile devices.
Be careful with free VPNs. VPN services are great. That's more than true. However, not universally across the board.
As someone once said,"if you're not paying for the product, then you're the product".And this is even more concerning considering that we're dealing with the topic of online privacy. At the end of the day, no one wants to have their data compromised or sold to a third party purely because they failed to read the fine-print when signing up for a seemingly great free VPN service.
6. Don't input sensitive personal data on non-HTTPs websites
In simple terms, HTTPS is the secure version of HTTP - the standard protocol that's used to send data between your web browser and the website you're reading.
Checking whether you're connected to a website via HTTPS is very simple. All you need to do is take a look at your browser's address bar and notice if the address starts with https://plus if there's a green padlock icon next to it.
The important thing to remember here is to never enter any sensitive information on websites that don't have HTTPS enabled. This includes things like your credit card information, social security numbers, address information, or anything else that you don't want to have compromised.
Unfortunately, there isn't "a fix" that you can do if a given website doesn't have HTTPS.
You simply have to avoid websites like that.
7. Clear your cookies regularly
Cookies are a popular term on the web, but very few people realize what they actually are. Technically speaking, cookies are quite simple. They're just small text files that are kept on your computer (and your mobile devices as well). They store small packets of information related to your personal activity in connection with a given website.
The most classic use of a cookie is to keep you logged in to a certain website and not force you to re-enter your credentials every time you come back. But cookies can go much further than that.
These days, they're also commonly used to store your shopping cart items (in case you decide to abandon your cart but then come back to the site later on and continue shopping), or to keep track of the content that you read previously on the site (thus helping with future content suggestions). These are just two of tens of possibilities.
Cookies are perhaps impossible to avoid entirely. If you disable them altogether, you're effectively making it nearly impossible for yourself to use sites like Facebook, Twitter, most e-commerce stores, or other services where login is required.
What you can do, though, is at least clear your cookies occasionally. This can help keep your browser clean and also not let some websites take advantage of older cookies that they set up maybe even months ago, thus making it more difficult to track your online habits.
8. Only use secure email
As we said above when discussing online messengers (in #6), email is not the most secure form of communication online. On the other hand, it's hard to image our life without email entirely, so, in some situations, we just need to bite the bullet and use email anyway.
However, there are still things that we can do to make it more secure.
First off, you can say goodbye to free email solutions like Gmail or Outlook.com, and instead opt for a premium one. One of the viable alternatives in that realm is ProtonMail.
Other than that, you can attempt to add another layer of encryption on top of your existing free email inbox. For instance, if you use Gmail, you can get this Chrome extensions, which will enable end-to-end encryption on your messages as well as attachments. This sort of encryption makes sure that your conversation remains private.
9. Review the permissions given to your mobile apps
Each app that you have on your iPhone, iPad, or Android device requires a certain set of permissions to deliver its functionality. Sometimes, though, certain apps become too demanding in this department, requesting access to more than seems necessary to make the app operational.
If you ever caught yourself wondering, "Why does a recipe app need access to my location all the time?" then you know what we're talking about.
What you should do from time to time is go through your currently installed apps and review the permissions given to them. Most of the time, you can revoke part of those permissions without making the app useless (like the recipe app example).
On iPhone, you can do that by going to Settings, scrolling to the bottom, and then going through each app one by one.
To view original article, click here.



